Libraries tagged by expire token generator
shetabit/token-builder
6191 Downloads
Laravel Token Builder
briqpay/php-sdk
10847 Downloads
This is the API documentation for Briqpay. You can find out more about us and our offering at our website [https://briqpay.com](https://briqpay.com) In order to get credentials to the playgrund API Please register at [https://app.briqpay.com](https://app.briqpay.com) # Introduction Briqpay Checkout is an inline checkout solution for your b2b ecommerce. Briqpay Checkout gives you the flexibility of controlling your payment methods and credit rules while optimizing the UX for your customers # SDKs Briqpay offers standard SDKs to PHP and .NET based on these swagger definitions. You can download them respively or use our swagger defintitions to codegen your own versions. #### For .NET `` Install-Package Briqpay `` #### For PHP `` composer require briqpay/php-sdk `` # Standard use-case As a first step of integration you will need to create a checkout session. \n\nIn this session you provide Briqpay with the basic information necessary. In the response from briqpay you will recieve a htmlsnippet that is to be inserted into your frontend. The snippet provided by briqpay will render an iframe where the user will complete the purchase. Once completed, briqpay will redirect the customer to a confirmation page that you have defined. 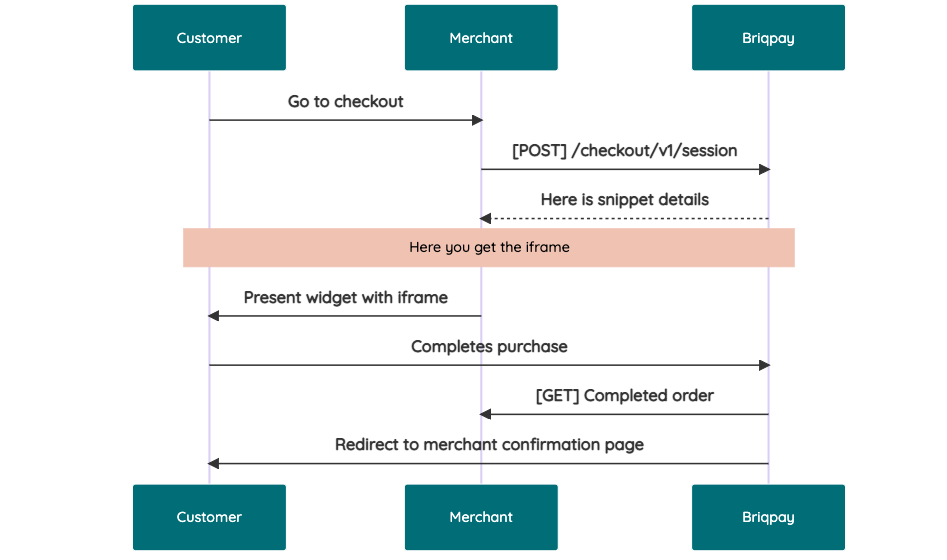 # JavaScript SDK The first step of integration is to add our JS to your site just before closing the ```` tag. This ensures that our JS library is avaliable to load the checkout. ```` Briqpay offers a few methods avaliable through our Javascript SDK. The library is added by our iframe and is avalable on ``window._briqpay`` If you offer the posibility to update the cart or order amonts on the checkout page, the JS library will help you. If your store charges the customer different costs and fees depening on their shipping location, you can listen to the ``addressupdate``event in order to re-calculate the total cost. ```javascript window._briqpay.subscribe('addressupdate', function (data) { console.log(data) }) ``` If your frontend needs to perform an action whe the signup has completed, listen to the ``signup_finalized`` event. ```javascript window._briqpay.subscribe('signup_finalized', function (status) { // redirect or handle status 'success' / 'failure' }) ``` If you allow customers to change the total cart value, you can utilise the JS library to suspend the iframe while you perform a backen update call towards our services. As described below: 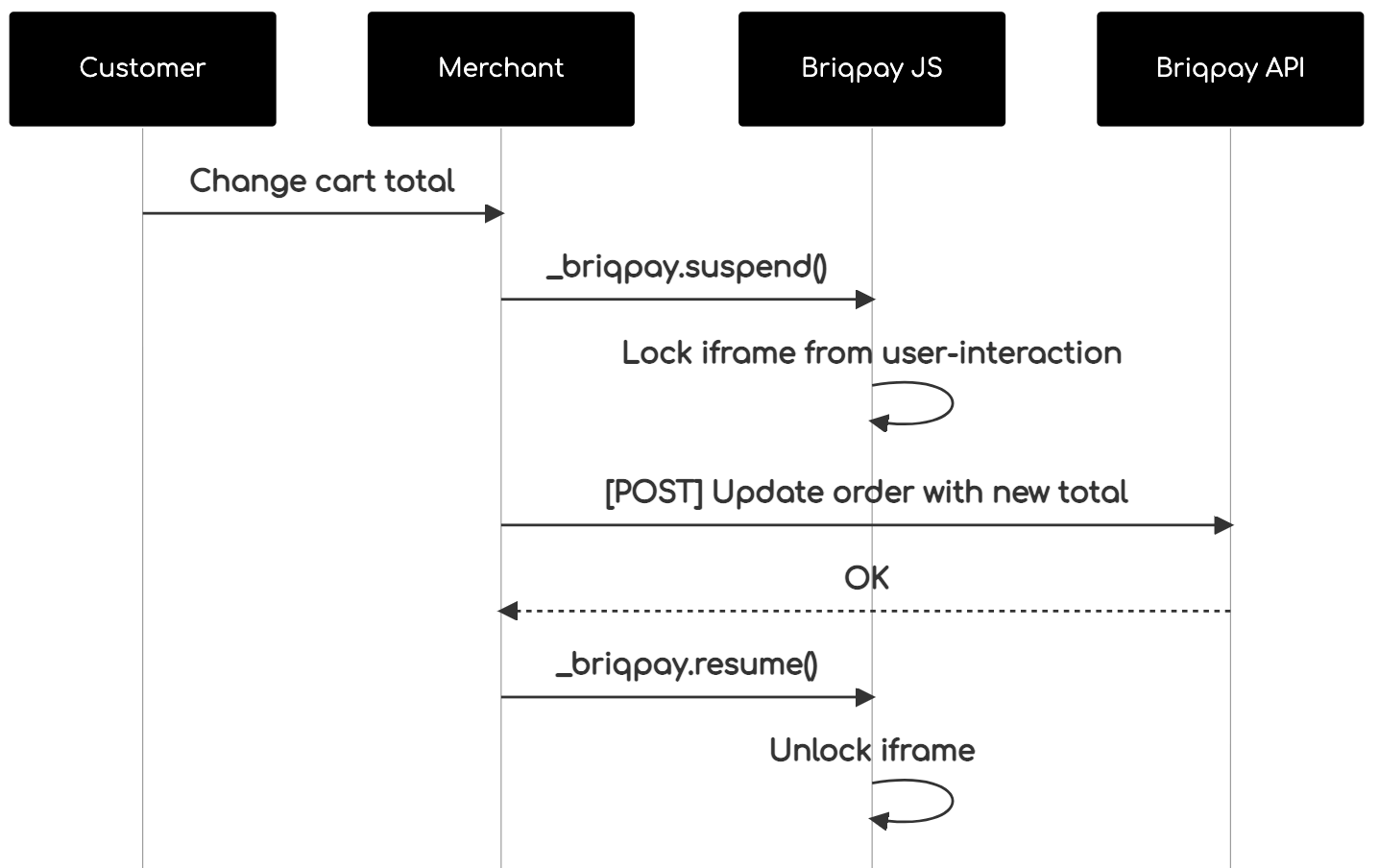 The iframe will auto-resume after 7 seconds if you dont call ``_briqpay.resume()`` before # Test Data In order to verify your integration you will neeed to use test data towards our credit engine. ## Company identication numbers * 1111111111 - To recieve a high credit scoring company ( 100 in rating) * 2222222222 - To test the enviournment with a bad credit scoring company (10 in rating) ## Card details In our playground setup your account is by default setup with a Stripe integration. In order to test out the card form you can use the below card numbers: * 4000002500003155 - To mock 3ds authentication window * 4000000000000069 Charge is declined with an expired_card code. You can use any valid expiry and CVC code # Authentication Briqpay utilizes JWT in order to authenticate calls to our platform. Authentication tokens expire after 48 hours, and at that point you can generate a new token for the given resource using the ``/auth`` endpoint. - Basic Auth - only used on the auth endpoint in order to get the Bearer Token - JWT Bearer Token - All calls towards the API utlizes this method"
martinmulder/openapi-crowdstrike-falcon-php
43 Downloads
Use this API specification as a reference for the API endpoints you can use to interact with your Falcon environment. These endpoints support authentication via OAuth2 and interact with detections and network containment. For detailed usage guides and examples, see our [documentation inside the Falcon console](https://falcon.eu-1.crowdstrike.com/support/documentation). To use the APIs described below, combine the base URL with the path shown for each API endpoint. For commercial cloud customers, your base URL is `https://api.eu-1.crowdstrike.com`. Each API endpoint requires authorization via an OAuth2 token. Your first API request should retrieve an OAuth2 token using the `oauth2/token` endpoint, such as `https://api.eu-1.crowdstrike.com/oauth2/token`. For subsequent requests, include the OAuth2 token in an HTTP authorization header. Tokens expire after 30 minutes, after which you should make a new token request to continue making API requests.
kruegge82/jtlffn
5 Downloads
# Introduction JTL-FFN is a standardized interface for fulfillment service providers and their customers. Fulfiller can offer their services to merchants and merchants can respectively choose from a wide range of service providers according to their needs. ## The ecosystem The FFN network consists of this REST API, an online portal and third party integrations (JTL-Wawi being one of them). The REST API orchestrates the interactions between the participants and the portal website provides services by JTL (such as managing and certifying warehouses of a fulfiller and merchants searching for their service providers). ## About this API The base url of this api is [https://ffn2.api.jtl-software.com/api](https://ffn2.api.jtl-software.com/api). This API (and this documentation) consists of three parts: * Fulfiller API - operations used when acting as a fulfiller in the network. Only users with the role `Fulfiller` can access these endpoints. * Merchant API - operations used when acting as a merchant in the network. Only users with the role `Merchant` can access these endpoints. * Shared API - operations available to all users. Please use the navigation menu at the top to switch between the documentation for the different APIs. # OAuth The FFN-API uses [OAuth2](https://tools.ietf.org/html/rfc6749) with the [Authorization Code Grant](https://tools.ietf.org/html/rfc6749#section-4.1) for its endpoints. Users must have an active [JTL customer center](https://kundencenter.jtl-software.de) account to authorize against the OAuth2 server. Applications and services using the API must acquire client credentials from JTL. ## Application credentials When making calls against the API, you need to do it in the context of an application. You will get the credentials for your application from JTL. Application credentials consist of the following: * `client_id` - uniquely identifies your application * `client_secret` - secret used to authenticate your application * `callback_uri` - the uri the OAuth2 server redirect to on authorization requests ## Requesting authorization When you want to authorize a user you redirect him to `https://oauth2.api.jtl-software.com/authorize` with the following query string parameters: * `response_type` - Must be set to "code" for the [Authorization Code Grant](https://tools.ietf.org/html/rfc6749#section-4.1). * `redirect_uri` - After the user accepts your authorization request this is the url that will be redirected to. It must match the `callback_uri` in your client credentials. * `client_id` - Your applications identifier from your application credentials. * `scope` - The scopes you wish to authorize (space delimited). * `state` - An opaque value that will be included when redirecting back after the user accepts the authorisation. This is not required, but is important for [security considerations](http://www.thread-safe.com/2014/05/the-correct-use-of-state-parameter-in.html). After successful authorization by the user, the OAuth2 server will redirect back to your applications callback with the following query string parameters: * `code` - The authorization code. * `state` - The state parameter that was sent in the request. ## Verifying authorization The authorization code you acquired in the last step will now be exchanged for an access token. In order to do this you need to POST a request to `https://oauth2.api.jtl-software.com/token`. >POST > >Authorization: Basic `application_basic_auth`\ >Content-Type: application/x-www-form-urlencoded > >grant_type=authorization_code&code=`code`&redirect_uri=`redirect_uri` In the Authorization header [Basic HTTP authentication](https://tools.ietf.org/html/rfc7617) is used. Your application credentials `client_id` will be used as the username and your `client_secret` as the password. The header should have the value "Basic" plus the Base64 encoded string comprising of `client_id:client_secret`. The body of the request consist of the form encoded parameters: * `grant_type` - Must be set to "authorization_code". * `code` - The authorization code received from the previous step. * `redirect_uri` - Must match the `callback_uri` in your client credentials. A successful verification request will return a JSON response with the properties: * `token_type` - is always "Bearer" * `expires_in` - the time in seconds until the access token will expire * `access_token` - the access token used for API requests * `refresh_token` - token used to get a new access_token without needing to ask the user again Now the APIs endpoints that need authorization can be called by setting the header >Authorization: Bearer `access_token` ## Refreshing authorization To get a new `access_token` (for example when the old one expired) one can POST a request to `https://oauth2.api.jtl-software.com/token`. >POST > >Authorization: Basic `application_basic_auth`\ >Content-Type: application/x-www-form-urlencoded > >grant_type=refresh_token&refresh_token=`refresh_token` The Basic HTTP Authorization works exactly as in the verification step. The body of the request consist of the form encoded parameters: * `grant_type` - Must be set to "refresh_token". * `refresh_token` - The `refresh_token` you acquired during verification. The response will be the same as in the verification step. ## Scopes Scopes allow fine grained control over what actions are allowed for a given application. During login users must approve the requested scopes, so it is often feasible to limit asking for permissions your application really needs. Global scopes for common permission scenarios are the following: * `ffn.fulfiller.read` - full read access for the fulfiller API * `ffn.fulfiller.write` - full write access for the fulfiller API * `ffn.merchant.read` - full read access for the merchant API * `ffn.merchant.write` - full write access for the merchant API More fine grained scopes can be acquired from each respective endpoints documentation. ## Example ### Prerequsites * JTL Customer center account (https://kundencenter.jtl-software.de/) * cUrl (https://curl.se/) * FFN portal account (just login here: https://fulfillment.jtl-software.com) * FFN portal sandbox account (if you want to test on sandbox: https://fulfillment-sandbox.jtl-software.com) * Oauth Client for authorization and define scopes Values in this example (access_token, refresh_token, code...) are expired and cannot be used verbatim. ### Step 1 - Create an OAuth client Navigate to https://kundencenter.jtl-software.de/oauth and create a new OAuth client. (You can´t navigate to Oauth in customer account, you should use this link, or you can change logged in index to oauth) !Templates define what scopes are possible for this client. scopes with access rights: * ffn.merchant.read - full read access for the fulfiller API * ffn.merchant.write - full write access for the fulfiller API * ffn.fulfiller.read - full read access for the merchant API * ffn.fulfiller.write - full write access for the merchant API More fine grained scopes can be acquired from each respective endpoints documentation.  Overview: clients, scopes, client-secret and client-id  In our example: * client_id: 97170e65-d390-4633-ba46-d6ghef8222de * client_secret: f364ldUw3wGJFGn3JXE2NpGdCvUSMlmK72gsYg1z * redirect_uri: http://localhost:53972/ffn/sso The values for this client should not be used in production and are for testing only. ### Step 2 - User login In this step you will redirect the user to the JTL OAuth website using his default browser. Here the user will provide his username/password and accept the requested scopes. Finally the JTL Oauth website will redirect to the provided redirect_uri and provide the code. Template: authorize specified scopes and get code answer to request the access token ``` https://oauth2.api.jtl-software.com/authorize?response_type=code&redirect_uri=[redirect_uri]&client_id=[client_id]&scope=[scopes] ``` Note: the scopes should be seperated by spaces or %20 Filled with our example values: ``` https://oauth2.api.jtl-software.com/authorize?response_type=code&redirect_uri=http://localhost:53972/ffn/sso/oauth&client_id=97170e65-d390-4633-ba46-d6ghef8222de&scope=ffn.merchant.read%20ffn.merchant.write ``` * enter password  * authorize scopes  * code answer from server  Example of the answer from the OAuth server to our redirect_uri: ``` http://localhost:53972/ffn/sso?code=def50200f3ac7aabbb6e82a6b131874115b858549dab62e73c68ea21a03de59b5744dc0f0ee321d7607062cf9bfa57471cd0ee7572db1d7b0a15779b0dda7d0ed8f8bfdb0f69939a34678d67aee41e4849d355d8aa223733ab1f397280b205fa739c6252d77d9ff600136e1b744352115fd62ba1035d8da4cbc1b6791c61d0bb621952b0a14625dd75807113ea0746e35528c304a8ce3c06724c1e1d9e1cb3709e9f52778bc8ca5b2d8f7c055f14244b1f8fcb61554c5bf48e02b882b87b9a76a43579eecd578cec97c6f603907e282e45cfec43837c063dc36b556d4974776a942f47cee19023e130ae852bfca6d3ca9c7cb3283d2bc4971f80651b626f8e7ba0ec2d13dddc4c528e1f3e470de907af7eb304d781534dd9b071d9760c9890e5756893c7800589c407bd2da3a2ff56c3fb15a410e24aa2df7ac54e8d0f7445e38e390171b58a0b66b337057d59acd29ed5bbc4df6bee921b244f030c86f49bcae21c9ca77c05eea0094414803f30089c39d585bf83604a2d9bbcc6442fbfdcff6cca946eb84d1eac2e4f98dff31a93460c951c853f9ef7140f572be963e82a3baf72afba34572af63ee7da ``` Extract the code and note it for next steps. ### Step 3 - Get an access_token from the code Template: get access token + refresh token ``` curl --location --request POST "https://oauth2.api.jtl-software.com/token" --header "Content-Type: application/x-www-form-urlencoded" -u "[client_id]:[client_secret]" --data-urlencode "grant_type=authorization_code" --data-urlencode "redirect_uri=[redirect_uri]" --data-urlencode "code=[code]" ``` Filled with our example values: ``` curl --location --request POST "https://oauth2.api.jtl-software.com/token" --header "Content-Type: application/x-www-form-urlencoded" -u "97170e64-d390-4696-ba46-d6fcef8207de:f364ldUw3wIJFGn3JXE2NpGdAvUSMlmK72gsYg1z" --data-urlencode "grant_type=authorization_code" --data-urlencode "redirect_uri=http://localhost:49420/oauth" --data-urlencode "code=def50200e6f3c65cfaba9419cbf6e48a7ed4324ef851b0ace493213884496b851fd825b90b4f994ee265a62f2358bbcbb0f990af5dbfd93dc63e51a7a6fa3bcfc7f722f56366b0a726fd1ed5df1cb926b16610fc7beb0f236e8858e86397422e3caa75d8094af8ba8ad6a93b938bd341bec1e4df671ad71ad1d5fa41166f5d4b2a3ac7d9172c35a8501f10ad722ec2aea88439c21b148ec2ba85e93c17acebe7d7f3d0118a50941cab145ed5ce92946426e5d388584556c0b010c567b433c577a1c4f7b1dfb2c99c25a0efadece4f64f19e54305bfc591e2b30b1a7ba1a33af3e039bcfa80b21ca365dc003f07989fca92472c2c8e2daab51151624a6a10bc511f2ed586f06544f7b98566df4667f5bbd6ba7c6707cb673c767c9eab5a74e63a8269688941c3158e8cc1cb5ebe9a8aa468faf415171a481ee1489b58bedb5fc329b23e0e34e76a4a500270fbebe4e1d20a0f17cebc96cd8ab3db383af746ca0699da34b4665afad30e9dde4f5f507a1dd14c73a692f06de8bafe3be81d7744dbcd8c5f7d3c767101ff5ce0556c244130c1c3fc3f53975a841c0cacebb70118f7552f50c2d2b1c421b8a21e" ``` The result will be a JSON answer with the users access_token and refresh_token as well as the expiry in seconds. ``` { "token_type":"Bearer", "expires_in":1800, "access_token":"eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9. eyJhdWQiOiI5NzE3MGU2NC1kMzkwLTQ2OTYtYmE0Ni1kNmZjZWY4MjA3ZGUiLCJqdGkiOiJlOWVhN2Q0MWI1NDIzNTcyYWU0MDEzYjEzMDZiMGRkNWM3YmQ2ZTNjMDNhYTZmNjQ2M2NlMjUzNTc0ZmUyMWE3NGQyNTIyMTJhODQwMmI1ZCIsImlhdCI6MTY2MTI1MzE0OCwibmJmIjoxNjYxMjUzMTQ4LCJleHAiOjE2NjEyNTQ5NDgsInN1YiI6IjQ2MjA5Iiwic2NvcGVzIjpbImZmbi5tZXJjaGFudC5yZWFkIiwiZmZuLm1lcmNoYW50LndyaXRlIl19.eEwY021wR3BWVp-wbAVQrjfqwFbYqLlOV_ca-cb7-O3Kdpi8mkFQBxfI8rzSiV_1WpAINf4ydV9FR9Ty992SMiAqGJ3T9zDHd68oUDePeq7Xfafp-87UboI2mCfGd7518CoKVLqg5ohb4YCqgC7Dz588FofggCQyDZQSM-8raOgcM-pJ1TT7oRuYuDHsOzCOTPcX2YiGYKCc3M6kxlBy_NjrJoLa4qysLRmPkznWwj0caC7a0VJO5KubvECcMb9D7Byr3UNjI7GiGMAufa770V5qCjrWs4gOsRV-Bn7oQydvsL21qqjBKHcssQrlLZWmrcfKqgBKwfRXIx3Mu5HBCmtHjHMnuvPVEZAj6fEfIwjYSeTAHTHApEwbE7J1MPd8MU0K6X2YEUF315fXN5F3rO3ZL5FdTwcM1E-1-PKubLuMAaE6Lw-QsDtBoI4ESylomCmCCfgLV4Vj-in_oCJUmKXAX0tDSa9y9vb6oAExung_BTJCBemffCtkJ55Px7bvi9JXmwvI0pIFo3QzTUtRbFDizCMrPZvsatFx64mXX3IDoVqXr3uzvdetBIJEj2ngVdGRrKGt4Yboae5oFV2d5jdSZBL28pwGjey__ZB4zLR1DodQ0sOqDWJ3WsEjMYXU8_-IGrS8Kkw8Q0R0UqqyVLfcLr-cfH5tYqf2QLqAScY","refresh_token":"def50200e636703f8d6372401e7b5e1163e0f46e5d593f6f8a1e9b1b2777d64684b87b7c552db62f9670bc482a3958d8aafb78083c7166c13f2f233fe4623d22873c819a560dc3213a51448a1e0763c2a0f7fb7230ceeae22a7fa84717458886584ab5a0ed1a500be5f9d3ed36b1d063d39b56c8431f3fe623055626c1f99f8c5b684853965645fe5c5bee941857aef79ae4f9b994316bec9d365119fe0fe8d035218c44d00a47c0e92b4613c1f388b9c171f3d79e45a6d2a52dfbd8d25608d6b0350420155e48cc179764a2432220cc0d1e9bfa7798050d0b36fe658e967186ea75cc1d1277cad973d43a0839c50b6885a87b5b446452855a00ac75c5f6d7f62b914496e30ab89a16b335977e4363b94dda7364bb052832a5d122696b6476fb0e1631030ea3c42d9659ca839cc44919efc9532c84f7170e634d3e189eb181d0c114ed9d8150c619f7567587e0311d89d51d1325646d2c014757ba7f2d7b02f7b56a52e093ed2ea95a8abe4a0289b24a5636dce8ad01c20e8cce8c4c51263e7f1731bb6335b0e31342e2439c77ab7cce7a147e24c9be9d61d8eba216fbfd4d5be2fba3502e69000ad6e67b7230a7f924" } ``` ### Step 4 - Test the access_token Using your newly aquired access_token you can test if its working (reminder: the access_token has a limited lifetime and might be expired, in which case we would need to refresh it (see Step 5)). Template: Test communication with access token on sandbox or production (our client is for both systems) ``` curl --location --request GET "https://ffn-sbx.api.jtl-software.com/api/v1/users/current" --header "Authorization: Bearer [access_token]" ``` If you cannot retrieve the user data using this endpoint make sure you have logged into our respective portal website (sandbox, production) at least once as this triggers user creation in the system. ### Step 5 - Refresh access_token when it expires Template: Get a new access token + refresh token with the refresh token ``` curl --location --request POST "https://oauth2.api.jtl-software.com/token" --header "Content-Type: application/x-www-form-urlencoded" -u "[client_id]:[client_secret]" --data-urlencode "grant_type=refresh_token" --data-urlencode "refresh_token=[refresh_token]" ``` Filled with our example values: ``` curl --location --request POST "https://oauth2.api.jtl-software.com/token" --header "Content-Type: application/x-www-form-urlencoded" -u "97170e64-d390-4696-ba46-d6fcef8207de:f364ldUw3wIJFGn3JXE2NpGdAvUSMlmK72gsYg1z" --data-urlencode "grant_type=refresh_token" --data-urlencode "refresh_token=def50200a01c0caff50b7db271f8268e3806ab2cce8e28e25f41e5fe9167a6521b47f6ed0dd3dd2d7856e1983ae645b032cf9285e91c1ee535decb0e0ca3e52670773f2737114955267d83db0204f80233214a623fcc36de04127e1cdcda006eaf60cacfb30c80081a8c9314e20117f64639ab5e333301a10173385c1bfc660709fde0b1a3517f8030dfdba8187e53c23c9d5fe9f33c48e11a4aa41bfd9ea1291507ea1bc8c64df32bdc91c61af907c41cf0bb305cae76e68448a85ad65b0a03a23ec35a7e9cc42aadd0792b9d7d187ae028e2759a7f4a0164f94d9baca29779a702f023216631e1e777069cc2bc65fd404f4fcc5818219063beb1717afe159b8110394af9a0d245de960c227b1183d6a745819ac08d92238938da798f702f83a3faf648f07a8a6d1e694c008517fd8be2fa154aab88a3eaacb3cbb1830c4bdee018e06c7f81e68c5844213f1d02372b23a22d99ac06a860748a3db891fd71768d74470c9a5a8571058dd901c888d13cd4481d63a800322614e63d3d8e6fb109ee7e1b1e046cd086ecbc2d4d362ca662e3ac867f21168833abd7a8247b06602197b7da555361efbf07b0afed69f7a558" ``` The result will be the same format as in step 3. Refresh_tokens are only valid for a single refresh and you will get a new refresh_token every single time that you must persist. ### My token is not working! #### 404 NotFound You need to log into the respective portal website (sandbox-https://fulfillment-sandbox.jtl-software.com, production-https://fulfillment.jtl-software.com) at least once to trigger user creation. #### 403 Forbidden You might be missing scopes in your token and don't have sufficient rights. #### 401 Forbidden Incorrect Oauth method. For example, we do not support the Oauth method authorisation "client_credentials grant". The authorisation method "code grant" with user must be used.
pdfgeneratorapi/php-client
208962 Downloads
# Introduction [PDF Generator API](https://pdfgeneratorapi.com) allows you easily generate transactional PDF documents and reduce the development and support costs by enabling your users to create and manage their document templates using a browser-based drag-and-drop document editor. The PDF Generator API features a web API architecture, allowing you to code in the language of your choice. This API supports the JSON media type, and uses UTF-8 character encoding. ## Base URL The base URL for all the API endpoints is `https://us1.pdfgeneratorapi.com/api/v4` For example * `https://us1.pdfgeneratorapi.com/api/v4/templates` * `https://us1.pdfgeneratorapi.com/api/v4/workspaces` * `https://us1.pdfgeneratorapi.com/api/v4/templates/123123` ## Editor PDF Generator API comes with a powerful drag & drop editor that allows to create any kind of document templates, from barcode labels to invoices, quotes and reports. You can find tutorials and videos from our [Support Portal](https://support.pdfgeneratorapi.com). * [Component specification](https://support.pdfgeneratorapi.com/en/category/components-1ffseaj/) * [Expression Language documentation](https://support.pdfgeneratorapi.com/en/category/expression-language-q203pa/) * [Frequently asked questions and answers](https://support.pdfgeneratorapi.com/en/category/qanda-1ov519d/) ## Definitions ### Organization Organization is a group of workspaces owned by your account. ### Workspace Workspace contains templates. Each workspace has access to their own templates and organization default templates. ### Master Workspace Master Workspace is the main/default workspace of your Organization. The Master Workspace identifier is the email you signed up with. ### Default Template Default template is a template that is available for all workspaces by default. You can set the template access type under Page Setup. If template has "Organization" access then your users can use them from the "New" menu in the Editor. ### Data Field Data Field is a placeholder for the specific data in your JSON data set. In this example JSON you can access the buyer name using Data Field `{paymentDetails::buyerName}`. The separator between depth levels is :: (two colons). When designing the template you don’t have to know every Data Field, our editor automatically extracts all the available fields from your data set and provides an easy way to insert them into the template. ``` { "documentNumber": 1, "paymentDetails": { "method": "Credit Card", "buyerName": "John Smith" }, "items": [ { "id": 1, "name": "Item one" } ] } ``` ## Rate limiting Our API endpoints use IP-based rate limiting and allow you to make up to 2 requests per second and 60 requests per minute. If you make more requests, you will receive a response with HTTP code 429. Response headers contain additional values: | Header | Description | |--------|--------------------------------| | X-RateLimit-Limit | Maximum requests per minute | | X-RateLimit-Remaining | The requests remaining in the current minute | | Retry-After | How many seconds you need to wait until you are allowed to make requests | * * * * * # Libraries and SDKs ## Postman Collection We have created a [Postman Collection](https://www.postman.com/pdfgeneratorapi/workspace/pdf-generator-api-public-workspace/overview) so you can easily test all the API endpoints without developing and code. You can download the collection [here](https://www.postman.com/pdfgeneratorapi/workspace/pdf-generator-api-public-workspace/collection/11578263-42fed446-af7e-4266-84e1-69e8c1752e93). ## Client Libraries All our Client Libraries are auto-generated using [OpenAPI Generator](https://openapi-generator.tech/) which uses the OpenAPI v3 specification to automatically generate a client library in specific programming language. * [PHP Client](https://github.com/pdfgeneratorapi/php-client) * [Java Client](https://github.com/pdfgeneratorapi/java-client) * [Ruby Client](https://github.com/pdfgeneratorapi/ruby-client) * [Python Client](https://github.com/pdfgeneratorapi/python-client) * [Javascript Client](https://github.com/pdfgeneratorapi/javascript-client) We have validated the generated libraries, but let us know if you find any anomalies in the client code. * * * * * # Authentication The PDF Generator API uses __JSON Web Tokens (JWT)__ to authenticate all API requests. These tokens offer a method to establish secure server-to-server authentication by transferring a compact JSON object with a signed payload of your account’s API Key and Secret. When authenticating to the PDF Generator API, a JWT should be generated uniquely by a __server-side application__ and included as a __Bearer Token__ in the header of each request. ## Accessing your API Key and Secret You can find your __API Key__ and __API Secret__ from the __Account Settings__ page after you login to PDF Generator API [here](https://pdfgeneratorapi.com/login). ## Creating a JWT JSON Web Tokens are composed of three sections: a header, a payload (containing a claim set), and a signature. The header and payload are JSON objects, which are serialized to UTF-8 bytes, then encoded using base64url encoding. The JWT's header, payload, and signature are concatenated with periods (.). As a result, a JWT typically takes the following form: ``` {Base64url encoded header}.{Base64url encoded payload}.{Base64url encoded signature} ``` We recommend and support libraries provided on [jwt.io](https://jwt.io/). While other libraries can create JWT, these recommended libraries are the most robust. ### Header Property `alg` defines which signing algorithm is being used. PDF Generator API users HS256. Property `typ` defines the type of token and it is always JWT. ``` { "alg": "HS256", "typ": "JWT" } ``` ### Payload The second part of the token is the payload, which contains the claims or the pieces of information being passed about the user and any metadata required. It is mandatory to specify the following claims: * issuer (`iss`): Your API key * subject (`sub`): Workspace identifier * expiration time (`exp`): Timestamp (unix epoch time) until the token is valid. It is highly recommended to set the exp timestamp for a short period, i.e. a matter of seconds. This way, if a token is intercepted or shared, the token will only be valid for a short period of time. ``` { "iss": "ad54aaff89ffdfeff178bb8a8f359b29fcb20edb56250b9f584aa2cb0162ed4a", "sub": "[email protected]", "exp": 1586112639 } ``` ### Payload for Partners Our partners can send their unique identifier (provided by us) in JWT's partner_id claim. If the `partner_id` value is specified in the JWT, the organization making the request is automatically connected to the partner account. * Partner ID (`partner_id`): Unique identifier provide by PDF Generator API team ``` { "iss": "ad54aaff89ffdfeff178bb8a8f359b29fcb20edb56250b9f584aa2cb0162ed4a", "sub": "[email protected]", "partner_id": "my-partner-identifier", "exp": 1586112639 } ``` ### Signature To create the signature part you have to take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that. The signature is used to verify the message wasn't changed along the way, and, in the case of tokens signed with a private key, it can also verify that the sender of the JWT is who it says it is. ``` HMACSHA256( base64UrlEncode(header) + "." + base64UrlEncode(payload), API_SECRET) ``` ### Putting all together The output is three Base64-URL strings separated by dots. The following shows a JWT that has the previous header and payload encoded, and it is signed with a secret. ``` eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhZDU0YWFmZjg5ZmZkZmVmZjE3OGJiOGE4ZjM1OWIyOWZjYjIwZWRiNTYyNTBiOWY1ODRhYTJjYjAxNjJlZDRhIiwic3ViIjoiZGVtby5leGFtcGxlQGFjdHVhbHJlcG9ydHMuY29tIn0.SxO-H7UYYYsclS8RGWO1qf0z1cB1m73wF9FLl9RCc1Q // Base64 encoded header: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9 // Base64 encoded payload: eyJpc3MiOiJhZDU0YWFmZjg5ZmZkZmVmZjE3OGJiOGE4ZjM1OWIyOWZjYjIwZWRiNTYyNTBiOWY1ODRhYTJjYjAxNjJlZDRhIiwic3ViIjoiZGVtby5leGFtcGxlQGFjdHVhbHJlcG9ydHMuY29tIn0 // Signature: SxO-H7UYYYsclS8RGWO1qf0z1cB1m73wF9FLl9RCc1Q ``` ## Temporary JWTs You can create a temporary token in [Account Settings](https://pdfgeneratorapi.com/account/organization) page after you login to PDF Generator API. The generated token uses your email address as the subject (`sub`) value and is valid for __15 minutes__. You can also use [jwt.io](https://jwt.io/) to generate test tokens for your API calls. These test tokens should never be used in production applications. * * * * * # Error codes | Code | Description | |--------|--------------------------------| | 401 | Unauthorized | | 402 | Payment Required | | 403 | Forbidden | | 404 | Not Found | | 422 | Unprocessable Entity | | 429 | Too Many Requests | | 500 | Internal Server Error | ## 401 Unauthorized | Description | |-------------------------------------------------------------------------| | Authentication failed: request expired | | Authentication failed: workspace missing | | Authentication failed: key missing | | Authentication failed: property 'iss' (issuer) missing in JWT | | Authentication failed: property 'sub' (subject) missing in JWT | | Authentication failed: property 'exp' (expiration time) missing in JWT | | Authentication failed: incorrect signature | ## 402 Payment Required | Description | |-------------------------------------------------------------------------| | Your account is suspended, please upgrade your account | ## 403 Forbidden | Description | |-------------------------------------------------------------------------| | Your account has exceeded the monthly document generation limit. | | Access not granted: You cannot delete master workspace via API | | Access not granted: Template is not accessible by this organization | | Your session has expired, please close and reopen the editor. | ## 404 Entity not found | Description | |-------------------------------------------------------------------------| | Entity not found | | Resource not found | | None of the templates is available for the workspace. | ## 422 Unprocessable Entity | Description | |-------------------------------------------------------------------------| | Unable to parse JSON, please check formatting | | Required parameter missing | | Required parameter missing: template definition not defined | | Required parameter missing: template not defined | ## 429 Too Many Requests | Description | |-------------------------------------------------------------------------| | You can make up to 2 requests per second and 60 requests per minute. | * * * * *
m-michalis/boxnow-api
983 Downloads
Document describes the API description for partners in order to create and track delivery requests. ## Revision history |Date|Author|Description|Version| |-|-|-|-| |2024-09-26|Hoffmann, P.| Add P466 error code |1.65| |2024-09-25|Filatov, R.| Add P465 error for /api/{v1,v2}/delivery-requests:checkAddressDelivery |1.64| |2024-08-13|Hoffmann, P.| Update `shippingRegions` in /api/v1/entrusted-partners response. |1.63| |2024-07-22|Hoffmann, P.| Add `shippingRegions` and `phoneNumber` to /api/v1/entrusted-partners response. |1.62| |2024-07-11|Filatov, R.| Add P461, P462, P464 errors for ArcGIS validations to /api/v2/delivery-requests:checkAddressDelivery |1.61| |2024-07-08|Hoffmann, P.| Add `email` and `phoneNumber` to /api/v1/entrusted-partners response. Add `originContactEmail` and `originContactNumber` to /api/v1/delivery-requests:fromCsv request body |1.60| |2024-05-23|Balagazova, K.| Add lost parcel event |1.59| |2024-04-08|Hoffmann, P.| Add declareDeliveryPartnerReturn |1.58| |2024-03-15|Šmolík, J.| Add generate upload label link |1.57| |2024-02-02|Šmolík, J.| Add location id to /api/v1/parcels events |1.56| |2023-11-15|Filatov, R.| Add P422, P423, P424 error codes |1.55| |2023-11-13|Filatov, R.| Add new `/api/v2/delivery-requests:checkAddressDelivery` endpoint switched to ArcGIS |1.54| |2023-11-08|Filatov, R.| Add `customerReturnsMaxAllowedSize` for /api/v1/entrusted-partners |1.53| |2023-06-10|Filatov, R.| Add `weight` min/max validation (error cde P421) and always round it to 2 decimals on /api/v1/delivery-requests:customerReturns|1.52| |2023-05-10|Balagazova, K.| Forbid usage of `q` parameter of `api/v1/parcels` for partner server accounts |1.51| |2023-04-28|Hoffmann, P.| Remove `X-Overwrite-Date` request header from /api/v1/delivery-requests and /api/v1/entrusted-partners |1.50| |2023-04-28|Azizov, J.| Add P442 error code |1.49| |2023-04-12|Balagazova, K.|Add `limit` field and automatic ordering by distance to /api/v1/destinations |1.48| |2023-04-04|Balagazova K.| Add `showRecipientInformation` field to /api/v1/delivery-requests /api/v1/delivery-requests:fromCsv |1.47| |2023-02-23|Balagazova K.| Add customer information to the webhook message |1.46| |2022-11-29|Azizov J.| Add Webhook schema and an example endpoint |1.45| |2022-11-28|Vala J.| Add partner permission to /entrusted-partners response |1.44| |2022-11-24|Vala J.| Add partner permission `addressAsDestination`, `codAddressAsDestination`. Validate partner permission for delivery to address and cod payment use for delivery to address when creating delivery request |1.43| |2022-11-14|Vala J.| Add `X-Overwrite-Date` request header for delivery request to test Croatian currency conversion, only testeable on dev |1.42| |2022-10-21|Vala J.| Add validation error code to /api/v1/simple-delivery-requests /api/v1/delivery-requests /api/v1/delivery-requests:customerReturns |1.41| |2022-09-22|Šmolík, J.|Add accepted-to-locker parcel event |1.40| |2022-09-08|Šmolík J.| Add support for user to choose partner they want to work with |1.39| |2022-08-10|Šmolík J.| Add /labels:search to download PDF labels for defined criteria |1.38| |2022-08-08|Azizov. J.| Add `region` field to /destinations and /origins endpoints |1.37| |2022-07-27|Vala J.| Add EP for listing shipping label data of parcels order /api/v1/delivery-requests/{orderNumber}/label |1.36| |2022-07-27|Vala J.| Add EP for listing shipping label data of parcel /api/v1/parcels/{id}/label |1.35| |2022-07-22|Vala J.| Add destination_public_id column to csv export of parcels |1.34| |2022-07-08|Vala J.| Add exportCsvUrl to headers ['X-export-url-csv'] to response from /api/v1/parcelsAdd endpoint to export parcels to csv file /ui/v1/parcels.csv |1.33| |2022-06-27|Vala J.| Add width and printerModel query parameters for zpl shipping labels for /api/v1/delivery-requests/{orderNumber}/label.{type} and /api/v1/parcels/{id}/label.{type} |1.32| |2022-06-17|Šmolík, J.| Allow to select return location for delivery request |1.31| |2022-05-25|Vala, J.| Add single labelUrlPdf to headers ['X-labels-url-pdf'] in response from /api/v1/delivery-requests:fromCsv |1.30| |2022-05-25|Vala, J.| Add EP to handle csv import orders printing of shipping label /ui/v1/delivery-requests/{orderImportsNumber}/label.pdf |1.29| |2022-05-20|Vala, J.| Add possibility to overwrite 4 rows in shipping label sender info to /api/v1/delivery-requests endpoint |1.28| |2022-05-04|Azizov, J.| Add state and created filters to to /api/v1/parcels endpoint |1.27| |2022-05-03|Azizov, J.| Add possibility to search parcels to /api/v1/parcels endpoint |1.26| |2022-04-27|Azizov, J.| Add /api/v1/delivery-requests:customerReturns for customer returns delivery requests |1.25| |2022-04-26|Vala, J.| Add createTime, updateTime to parcel list response |1.24| |2022-04-21|Šmolík, J.| Add payment info to parcels |1.23| |2022-02-22|Azizov, J.| Add P408 and P409 error codes |1.22| |2022-02-22|Azizov, J.| Add notifySMSOnAccepted to DeliveryRequest |1.21| |2022-02-01|Šmolík, J.| Add check address delivery endpointAdd /api/v1/simple-delivery-requests for simpler delivery creation |1.20| |2022-01-20|Šmolík, J.| Add P405, P406 and P407 error codes |1.19| |2022-01-10|Šmolík, J.| Add CSV import endpointAdd JWT custom claims descriptionMove 403 error codes to own section |1.18| |2021-12-23|Šmolík, J.| Add new endpoint to confirm AnyAPM delivery of a parcelPartition error codes by HTTP status response |1.17| |2021-12-16|Šmolík, J.| Add new error code P403 |1.16| |2021-12-09|Šmolík, J.| Add new error codes P401, P402 |1.15| |2021-11-30|Šmolík, J.| Add delivery request origin, destination and items fields description |1.14| |2021-11-11|Šmolík, J.| Add endpoint for parcel delivery cancellation |1.13| |2021-11-09|Šmolík, J.| Add X403 error code spec |1.12| |2021-10-14|Šmolík, J.| Add Accepted for return event |1.11| |2021-10-05|Šmolík, J.| Make DeliveryRequest.items required |1.10| |2021-09-22|Šmolík, J.| Add canceled event state and event|1.9| |2021-09-17|Šmolík, J.| Add PDF label URLs to parcels response |1.8 |2021-09-13|Šmolík, J.| Update parcel state enum valuesRemove history event displayName, add type|1.7 |2021-08-25|Azizov, J.| Add possibility to print labels for all parcels in orderMake contact information of origin optional in delivery request|1.6 |2021-08-02|Azizov, J.| Add items metadata to parcel |1.5| |2021-07-15|Šmolík, J.| Add destination expected delivery time |1.4| |2021-06-23|Šmolík, J.| Update money value fields description |1.3| |2021-06-21|Šmolík, J.| Update Requesting a delivery textAdd `name` filter to origins and destinations Rename delivery request code of description to plain descriptionAdd more specific info to value amount fieldsUpdate address country to match ISO CodeUpdate address postal code formattingUpdate origin/destination for delivery requestRemove height, length, width from order itemAdd events to parcel infoUpdate delivery request responseUpdate order number descriptionAdd parcel id filter to /parcelsAdd message to errorMake contact name requiredAdd delivery partner parcel idsRemove order items' code and status |1.2| |2021-06-14|Šmolík, J.| Add a todo to specify client notification type after accepting the order. Let the partner choose to receive an email when successful delivery request is made. Remove `typeOfOrder` from delivery request.Add option to select delivery partner for pickupMake item weight in the order optionalMake origin contact email requiredAdd support to add sender's name when making delivery requestRemove landmark and code from addressAdd new error code or partners not eligible to create COD delivery requestsAdd support to filter destinations/origins by typeAdd support to send compartment size for order item, required for APM originMake `typeOfService` optional |1.1| |2021-06-09|Šmolík, J.|Initial version|1.0| # Setup Register your company through our support. We are going to need - Company name - List of Phone numbers for SMS OTP authentication of people who'll you want to have access to the Partner CMS - List of addresses for pickup points - where do we pickup your order for delivery You will get in return - `OAUTH_CLIENT_ID` - OAuth2 Client ID for authenticating with the Partner API. Keep it safe. Value may vary for each environment. - `OAUTH_CLIENT_SECRET` - OAuth2 Client Secret for authenticating with the Partner API. Keep it safe. Value may vary for each environment. - `API_URL` - Base URL for Partner API ## Environments Product offers multiple environments - Sandbox - For you to test the integration. Limited functionality. - Production - Connected to real end-users. Use with care. Environment setting summary: | Value \ Env | Sandbox | Production | |---|---|---| | `API_URL` | N/A | N/A | | `OAUTH_CLIENT_SECRET` | Contact Support | Contact Support | | `OAUTH_CLIENT_ID` | Contact Support | Contact Support | # API ## Authentication Authentication is based on OAuth2 standard, Client Credentials grant. Token endpoint `/auth-sessions`, see examples below. Client ID and Secret MUST be passed to you from BoxNow support in advance. In order to use the API, you MUST attach the access token to Authorization header as a Bearer token. ### Custom JWT claims You can find additional user information in custom claims under namespace key `https://boxnow.gr`. For example ```json { "iat": 1641980553, "exp": 1641984153, "https://boxnow.gr": { "permission": { "warehouseAsOrigin": true, "anyApmAsOrigin": true, "anyApmToSameApmDelivery": true, "anyApmToSameApmDeliveryWithoutConfirmation": true, "depotAsOrigin": true } } } ``` ## Listing available destinations You can skip this if you don't want to deliver your order to one of our APMs. Use `/destinations` to list available APM locations we can deliver the goods to. You will refer to these records by `id` when requesting delivery later on. ## What can influence `/destinations` endpoint response - Only APMs with `Box Now Ready` state are considered - APMs must be available for your required package size (see: '#/components/parameters/LocationRequiredSize') ## Requesting a delivery Create a delivery request to delivery your order to the client. Use `/delivery-requests` endpoint for this operation. Once a successful request delivery is made - (optional) we send you an email notifying about successful delivery request creation, if you choose to receive this email - you should fetch the PDF label for each of the parcel from `/parcels/{id}/label.pdf`, print it and stick it to the parcel/s - we send a courier to pick up the labeled parcel/s - we notify the client via email that we have accepted the order from you and its being delivered by us ## Modifying a delivery request After a delivery request is successfully made, you can alter some parts of it later on. Use `/delivery-requests/{id}` endpoint for these modifications. ## Checking on the deliveries You can list parcel related to your delivery requests via `/parcels` endpoint. ## Error codes ### Description of codes for `400 Bad Request` responses - `P400` - Invalid request data. Make sure are sending the request according to this documentation. - `P401` - Invalid request origin location reference. Make sure you are referencing a valid location ID from Origins endpoint or valid address. - `P402` - Invalid request destination location reference. Make sure you are referencing a valid location ID from Destinations endpoint or valid address. - `P403` - You are not allowed to use AnyAPM-SameAPM delivery. Contact support if you believe this is a mistake. - `P404` - Invalid import CSV. See error contents for additional info. - `P405` - Invalid phone number. Make sure you are sending the phone number in full international format, e.g. +30 xx x xxx xxxx. - `C404` - Invalid phone number. Make sure you are sending the phone number in full international format, e.g. +30 xx x xxx xxxx. - `P406` - Invalid compartment/parcel size. Make sure you are sending one of required sizes 1, 2 or 3. Size is required when sending from AnyAPM directly. - `P407` - Invalid country code. Make sure you are sending country code in ISO 3166-1 alpha-2 format, e.g. GR. - `P408` - Invalid amountToBeCollected amount. Make sure you are sending amount in the valid range of (0, 5000> - `P409` - Invalid delivery partner reference. Make sure you are referencing a valid delivery partner ID from Delivery partners endpoint. - `P410` - Order number conflict. You are trying to create a delivery request for order ID that has already been created. Choose another order id. - `P411` - You are not eligible to use Cash-on-delivery payment type. Use another payment type or contact our support. - `P412` - You are not allowed to create customer returns deliveries. Contact support if you believe this is a mistake. - `P413` - Invalid return location reference. Make sure you are referencing a valid location warehouse ID from Origins endpoint or valid address. - `P415` - You are not allowed to create delivery to home address. Contact support if you believe this is a mistake. - `P416` - You are not allowed to use COD payment for delivery to home address. Contact support if you believe this is a mistake. - `P417` - You are not allowed to use `q` parameter. It is forbidden for server partner accounts. - `P420` - Parcel not ready for cancel. You can cancel only new, undelivered, or parcels that are not returned or lost. Make sure parcel is in transit and try again. - `P421` - Invalid parcel weight. Make sure you are sending value between 0 and 10^6. - `P422` - Address not found. Try to call just with postal code and country. - `P423` - Nearby locker not found. - `P424` - Invalid region format. Please ensure the format includes a language code followed by a country code in ISO 3166-1 alpha-2 format, separated by a hyphen, e.g. el-GR, or region exists in context. - `P425` - Parcel not ready to declare a delivery partner return. Make sure parcel is not in any of the following states in order to declare a delivery partner return: 'canceled-return', 'lost', 'canceled', 'returned', 'expired-return'. - `P426` - Parcel not eligible to declare a delivery partner return. Parcel needs to use a delivery partner in order to declare a return. - `P430` - Parcel not ready for AnyAPM confirmation. Parcel is probably already confirmed or being delivered. Contact support if you believe this is a mistake. - `P440` - Ambiguous partner. Your account is linked to multiple partners and is unclear on whose behalf you want to perform this action. Send `X-PartnerID` header with ID of the partner you want to manage. You can get list of available Partner IDs from /entrusted-partners endpoint. - `P441` - Invalid X-PartnerID header. Value you provided for X-PartnerID header is either invalid or references partner you don't have access to. Make sure you are sending ID from /entrusted-partners endpoint. - `P442` - Invalid limit query parameter. The query limit for this API has been exceeded. Please reduce the size of your query (max allowed is 100). - `P460` - Parcel not eligible for external destination delivery. Delivery request destination.deliveryPartnerId is not set. - `P461` - Invalid street. Make sure the length is not more than 100 characters. - `P462` - Invalid city. Make sure the length is not more than 50 characters. - `P464` - Invalid postal code. Make sure the length is not more than 20 characters. ### Description of codes for `403 Forbidden` responses - `X403` - Account disabled. Your account had been disabled, contact support. - `P414` - Unauthorized parcel access. You are trying to access information to parcel/s that don't belong to you. Make sure you are requesting information for parcels you have access to. - `P465` - Partner doesn't have access for checking delivery addresses. - `P466` - You are not allowed to create a delivery request because your account has an overdue flag and you are not a vip partner. ### Description of codes for `503 Service Unavailable` responses | Code | Description | |---|---| | `P600` | Locker bridge communication failed. There has been some error when communicating with the locker bridge. Try again later or contact support. | | `P610` | Geolocation API failed. There has been some error when translating address to gps coordinates. Try again later or contact support. |
daphascomp/daphascompsms
2 Downloads
# Authentication Requests made to our APIs must be authenticated, there are two ways to do this: 1. Authenticating using your API apiUsername and apiPassword - `Basic Auth` 2. Authenticating using an Auth Token - `Bearer Token` ## Method 1: Basic Auth Basic Authentication is a method for an HTTP user agent (e.g., a web browser) to provide a apiUsername and apiPassword when making a request. When employing Basic Authentication, users include an encoded string in the Authorization header of each request they make. The string is used by the request’s recipient to verify users’ identity and rights to access a resource. The Authorization header follows this format: > Authorization: Basic base64(apiUsername:apiPassword) So if your apiUsername and apiPassword are `onfon` and `!@pas123`, the combination is `onfon:!@pas123`, and when base64 encoded, this becomes `b25mb246IUBwYXMxMjM=`. So requests made by this user would be sent with the following header: > Authorization: Basic b25mb246IUBwYXMxMjM= | Description | | ---------------------------------------------------------------------------------------------- | | **apiUsername** `String` `Required` Your onfon account apiUsername, retrieved from portal | | **apiPassword** `String` `Required` Your onfon account apiPassword, retrieved from portal | ## Method 2: Bearer Tokens This authentication stategy allows you to authenticate using JSON Web Token ``JWT` that will expire after given duration. Each Access Token is a `JWT`, an encoded JSON object with three parts: the `header`, the `payload`, and the `signature`. The following is an example Access Token generated for Conversations > Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c ### Getting the token To generate the token, make a `POST` request to `/v1/authorization` endpoint with your `apiUsername` and `apiPassword` This request should be made from your server and not on the client side such as browser or mobile environment. You will receive a JSON similar to below: `{ "token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c", "validDurationSeconds": 3600}` You can use the token received to make API calls. The token will be valid for value of `validDurationSeconds`, before which you should generate a new token. #### Request Body ``` { "apiUsername": "root", "apiPassword": "hakty11" } ``` #### Response Body ``` { "token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c", "validDurationSeconds": 3600 } ``` #### Example Curl ``` curl --location --request POST 'https://apis.onfonmedia.co.ke/v1/authorization' \ --data-raw '{ "apiUsername": "correctapiUsername", "apiPassword": "correctapiPassword" } ``` #### Making an API call You will be required to pass the token in `Authorization` header prefixed by `Bearer` when calling other endpoints. Example `Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c`