Libraries tagged by http auth
forrest79/dev-certs
730 Downloads
Create SSL wildcards domain certificates with own certificate authority for and ONLY for development.
delight-im/otp
396 Downloads
One-time password (OTP) implementation for two-factor authentication with TOTP in accordance with RFC 6238 and RFC 4226
chillerlan/php-googleauth
1310 Downloads
A generator for counter- and time based 2-factor authentication codes (Google Authenticator). PHP 8.2+
vira/hpropagate
2042 Downloads
Symfony bundle for propagating http headers from incoming requests to the corresponding outgoing requests automatically
briqpay/php-sdk
10565 Downloads
This is the API documentation for Briqpay. You can find out more about us and our offering at our website [https://briqpay.com](https://briqpay.com) In order to get credentials to the playgrund API Please register at [https://app.briqpay.com](https://app.briqpay.com) # Introduction Briqpay Checkout is an inline checkout solution for your b2b ecommerce. Briqpay Checkout gives you the flexibility of controlling your payment methods and credit rules while optimizing the UX for your customers # SDKs Briqpay offers standard SDKs to PHP and .NET based on these swagger definitions. You can download them respively or use our swagger defintitions to codegen your own versions. #### For .NET `` Install-Package Briqpay `` #### For PHP `` composer require briqpay/php-sdk `` # Standard use-case As a first step of integration you will need to create a checkout session. \n\nIn this session you provide Briqpay with the basic information necessary. In the response from briqpay you will recieve a htmlsnippet that is to be inserted into your frontend. The snippet provided by briqpay will render an iframe where the user will complete the purchase. Once completed, briqpay will redirect the customer to a confirmation page that you have defined. 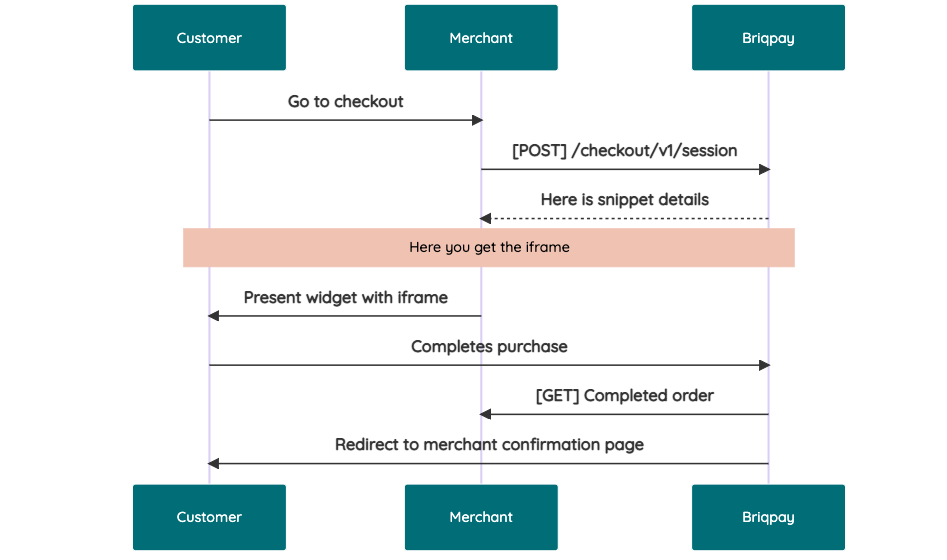 # JavaScript SDK The first step of integration is to add our JS to your site just before closing the ```` tag. This ensures that our JS library is avaliable to load the checkout. ```` Briqpay offers a few methods avaliable through our Javascript SDK. The library is added by our iframe and is avalable on ``window._briqpay`` If you offer the posibility to update the cart or order amonts on the checkout page, the JS library will help you. If your store charges the customer different costs and fees depening on their shipping location, you can listen to the ``addressupdate``event in order to re-calculate the total cost. ```javascript window._briqpay.subscribe('addressupdate', function (data) { console.log(data) }) ``` If your frontend needs to perform an action whe the signup has completed, listen to the ``signup_finalized`` event. ```javascript window._briqpay.subscribe('signup_finalized', function (status) { // redirect or handle status 'success' / 'failure' }) ``` If you allow customers to change the total cart value, you can utilise the JS library to suspend the iframe while you perform a backen update call towards our services. As described below: 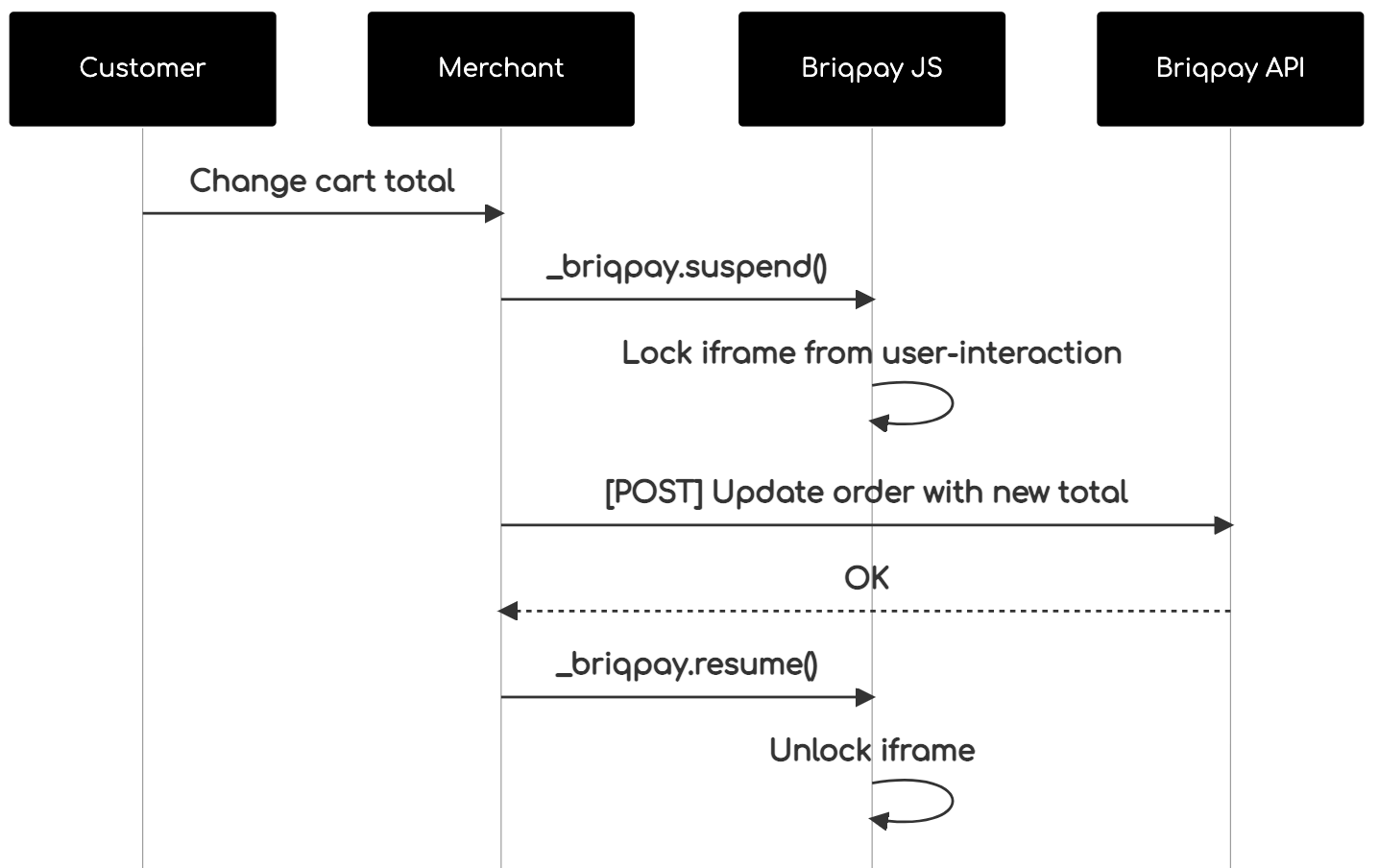 The iframe will auto-resume after 7 seconds if you dont call ``_briqpay.resume()`` before # Test Data In order to verify your integration you will neeed to use test data towards our credit engine. ## Company identication numbers * 1111111111 - To recieve a high credit scoring company ( 100 in rating) * 2222222222 - To test the enviournment with a bad credit scoring company (10 in rating) ## Card details In our playground setup your account is by default setup with a Stripe integration. In order to test out the card form you can use the below card numbers: * 4000002500003155 - To mock 3ds authentication window * 4000000000000069 Charge is declined with an expired_card code. You can use any valid expiry and CVC code # Authentication Briqpay utilizes JWT in order to authenticate calls to our platform. Authentication tokens expire after 48 hours, and at that point you can generate a new token for the given resource using the ``/auth`` endpoint. - Basic Auth - only used on the auth endpoint in order to get the Bearer Token - JWT Bearer Token - All calls towards the API utlizes this method"
aedart/athenaeum-http-api
1046 Downloads
Json based API utilities
mingalevme/retryable-psr-http-client
143 Downloads
The package provides a familiar PSR HTTP Client interface with automatic retries and exponential backoff (and others strategies). It is a thin wrapper over the standard PSR HTTP Client and exposes same public API. This makes the decorator very easy to drop into existing programs.
wildwolf/wp-two-factor-auth
128 Downloads
WordPress plugin for two factor authentication
siment/module-http-header-theme-switch
134 Downloads
Magento 2 module that enables automatic theme switching based on the X-UA-Device HTTP header. (Or any other header)
diggin/diggin-http-charset
3064 Downloads
Detecting based on header's charset and html meta charset. Automatically convert to UTF-8.
brunodebarros/http-request
207 Downloads
A web crawler, built to be easily dropped into PHP applications, which behaves just like a regular web browser, interpreting location redirects and storing cookies automatically.
aedart/athenaeum-filters
1752 Downloads
Search filter utilities, based on http query parameters
aedart/athenaeum-etags
1063 Downloads
ETags utilities and Http Conditional Request evaluation for your Laravel Application
eustasy/authenticatron
7 Downloads
HOTP / TOTP secrets with corresponding QR links and code verification from a simple PHP script.
sam002/yii2-otp
905 Downloads
YII2 extension for generating one time passwords according to RFC 4226/6238 (HOTP/TOTP Algorithm) and authentication widget